Security in DNA Data Storage: Cyber Risks in Biological Computing
- Swarnali Ghosh

- Jun 12
- 6 min read
SWARNALI GHOSH | DATE: JUNE 11, 2025
Introduction: The Future of Data Storage Lies in DNA

Picture compressing the vast expanse of the internet into a tiny fragment no larger than a sugar cube. Scientists and tech giants like Microsoft and IBM are turning to DNA data storage—a revolutionary method that encodes digital information into synthetic DNA molecules. With its unparalleled density (a single gram of DNA can store 215 petabytes of data) and longevity (DNA can last thousands of years if preserved properly), this technology could solve the world’s exploding data storage crisis. But with great innovation comes great risk. As DNA-based storage and biological computing evolve, so do cyber-biosecurity threats. Hackers could exploit synthetic DNA to deliver malware, steal genetic data, or even engineer biological weapons. The intersection of biology and cybersecurity—dubbed "cyber-biosecurity"—is now a critical frontier in data protection. The concept of storing information in DNA has moved beyond the realm of science fiction into scientific reality. With its staggering potential—storing the entire world’s data in a few grams of DNA—this emerging ecosystem is set to redefine archival memory systems. But as genomic technologies converge with digital systems, a new frontier of security concerns spans both cyber and biological realms. This piece delves into the emerging risks linked to DNA-based data storage and biological computing, while outlining measures to defend against these advancing threats.
Why DNA Storage? The Promise and the Peril
Unmatched density and longevity: DNA offers remarkable data density—petabytes per gram—and the potential for millennia-long stability under proper conditions. This taps into a growing need for sustainable, high-capacity archives as global data volumes explode.
Gateway to biological computing: Beyond storage, DNA is becoming a computing medium: programmable logic, encryption keys, even blockchain hybridization. But the biological interface introduces new attack vectors that sidestep traditional cybersecurity defenses.
How DNA Data Storage Works: From Binary to Biology
Traditional computers store data in binary code (0s and 1s). DNA, however, uses four nucleotide bases: Adenine (A), Thymine (T), Cytosine (C), Guanine (G). By converting digital data into sequences of these bases, researchers can encode vast amounts of information in microscopic DNA strands. For example:
DNA Data Storage:
Text files: Converted to A, T, C, G sequences.
Images & videos: Encoded in synthetic DNA molecules.
Databases: Stored in DNA libraries that last centuries.
The Process: Writing, Storing, and Reading DNA Data
Encoding: Algorithms translate binary data into DNA sequences.
Synthesis: Machines chemically construct the DNA strands.
Storage: DNA can be preserved in cold, dry conditions (like fossilized bones).
Retrieval: The DNA is read through sequencing, allowing the encoded information to be converted back into digital data.
Microsoft’s DNA Storage Project has already demonstrated this by encoding books, videos, and even entire operating systems into DNA. But while the technology is groundbreaking, it also opens the door to unprecedented cyber risks.
Real-World Vulnerabilities
Acoustic Side-Channel Eavesdropping: Researchers at UC Irvine and UC Riverside demonstrated that audio recordings of DNA synthesizers can reveal specific base sequences (“A, T, C, G”) using machine learning — a breach named Oligo Snoop. While still nascent, this attack signals how seemingly innocuous lab noise can compromise intellectual property or sensitive archival codes.
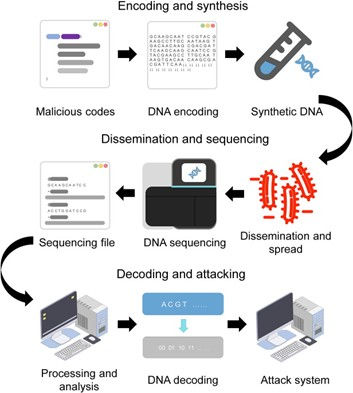
Malware Embedded in DNA: In a chilling proof-of-concept, a University of Washington team encoded malware into DNA strands so that sequencers treating DNA as data executed malicious commands (via a buffer overflow in FASTQ files). This “DNA malware” hack shows how malicious DNA can compromise sequencing software and downstream systems.
Lab and Cloud Infrastructure Attacks: Sequencer-connected systems—including laptops, network storage, and cloud APIs—are susceptible to standard cyberattacks: Firmware implants in sequencing equipment or infected PCs. Software supply-chain vulnerabilities in bioinformatics tools, where malicious updates can unlock remote control. Cloud misconfigurations in laboratory information management systems (LIMS) leading to genetic data leaks. Credential stuffing in direct-to-consumer genotyping giants (e.g., 23andMe lost data on 5.5–6.9 million users due to credential reuse.)
The Stakes Are High:
Privacy overload: DNA encodes uniquely identifying and sensitive traits. When this data is breached, it remains irrevocably exposed.
Industrial espionage & IP theft: Synthetic biology companies rely on proprietary sequences worth millions. Acoustic and remote theft undermines vital R&D.
Bioweapons potential: The same techniques used to store data in DNA could be misused to build harmful biological agents—raising national security alarms.

Widespread disruption: A firmware hack in widely deployed sequencers could cripple public health monitoring and agricultural sequencing globally.
Emerging Security Disciplines: Cyber-biosecurity
Cyber-biosecurity is a growing field focused on protecting the intersection of digital systems and biological assets, from sequencing machines to DNA data pipelines. As DNA’s use expands into computing and archival domains, so too must our security frameworks.
Building a Robust Defense
Cyber and Physical Lab Security: Air-gapping sequencers and using secure media-only data transfer. Note that even this can be compromised via firmware. Firewall and network controls, with strict segmentation for sequencing systems.
Authentication & Access Control: Multi-Factor Authentication (MFA) and robust credential hygiene are essential—protect cloud, LIMS, and lab equipment. Role-based permissions and digital signing of data and processing pipelines to prevent rogue sequences or software.
Encryption & Integrity: Data encryption at rest and in transit, including biological sequences and FASTQ/FASTA files. DNA cryptography involves integrating encryption directly within genetic sequences, using techniques like cipher-primers and DNA origami structures to enhance data protection.
Malware Detection in DNA: Pre-synthesis screening intercepts malicious payloads before production. Entropy and machine learning-based monitoring to detect anomalies during synthesis or sequencing.

Supply-Chain Hardening: Ensure sequencing hardware, cartridges, reagents, and software are supplied only via trusted sources. Regular vulnerability scanning for firmware and software, with prompt patching.
Governance and Policy: Implement clear biosecurity regulations, ideally certified by bodies like NIST. Encourage industry-wide standards for cyber-biosecurity—drawing from frameworks for cloud, IoT, and medical devices.
Training & Cross-Discipline Awareness: Educate staff on combined cyber and bio hazards—e.g., acoustic side-channels, biohacking, credential stuffing. Foster
collaboration between IT and security teams, lab scientists, and national authorities.
Insider Threats & Nation-State Attacks: Lab personnel could intentionally corrupt DNA samples. Nation-states might target genomic databases for espionage (e.g., stealing research on CRISPR-based medicine). Bio-terrorists could exploit DNA synthesis tools to engineer dangerous pathogens.
Looking Ahead

As DNA data storage and biological computing systems scale, so will the sophistication of cyber-bio threats. Key priorities going forward: Standardizing cyber-biosecurity frameworks that are internationally recognized. Continuous research into signal-based attacks (e.g., thermal, acoustic, electromagnetic) on lab equipment. Global collaboration between governments, academia, and private firms—to prevent single-point failures and asymmetric threats. Future protocols embedding encryption and authentication at the DNA molecule level.
Conclusion: The Double-Edged Sword of DNA Computing
DNA data storage could reshape the future of information technology, but it also introduces unprecedented cyber-biosecurity risks. From DNA malware to genetic identity theft, the stakes have never been higher. A comprehensive security approach that merges artificial intelligence, cryptographic methods, decentralized ledger technology, and robust regulatory frameworks. As we step into this brave new world, one thing is clear: Protecting our genetic code is just as important as protecting our digital one. DNA's emergence as a revolutionary storage medium comes with dual challenges: a promising future of ultra-dense, long-lasting archives—and a new risk landscape where biology and cyber fraud bits collide. From acoustic eavesdropping to malicious DNA payloads, the threats are real and evolving. Organizations stepping into the DNA data era must shift from traditional IT security to a hybrid cyber-bio approach, integrating physical, biological, and digital safeguards. Only then can we exploit DNA’s unparalleled advantages without compromising privacy, safety, or innovation.
Citations/References
De Silva, P. Y., & Ganegoda, G. U. (2016). New trends of digital data storage in DNA. BioMed Research International, 2016, 1–14. https://doi.org/10.1155/2016/8072463
Nexxant. (2025, May 26). Biological computing explained: what it is, how it works, applications, and the future. Nexxant Tech. https://www.nexxant.com.br/en/post/biological-computing-explained-what-it-is-how-it-works-applications-and-the-future#google_vignette
Tavella, F., Giaretta, A., Conti, M., & Balasubramaniam, S. (2020, September 28). A machine learning-based approach to detect threats in Bio-Cyber DNA storage systems. arXiv.org. https://arxiv.org/abs/2009.13380
Sunkesula, B. (2025, May 29). Biological data privacy: the next frontier in cybersecurity challenges. Tek Leaders. https://tekleaders.com/biological-data-privacy-cybersecurity-challenges/
Schumacher, G. J., Sawaya, S., Nelson, D., & Hansen, A. J. (2020). Genetic information insecurity as state of the art. Frontiers in Bioengineering and Biotechnology, 8. https://doi.org/10.3389/fbioe.2020.591980
Pulivarti, R. (2025, March 18). How secure is your DNA? NIST. https://www.nist.gov/blogs/taking-measure/how-secure-your-dna
Liu, T., Zhou, S., Wang, T., & Teng, Y. (2024). Cyberbiosecurity: Advancements in DNA-based information security. Biosafety and Health, 6(4), 251–256. https://doi.org/10.1016/j.bsheal.2024.06.002
Image Citations
Rakshitakitra. (2025, February 4). Cybersecurity challenges in DNA data Storage - Akitra. https://akitra.com/cybersecurity-challenges-in-dna-data-storage/
Liu, T., Zhou, S., Wang, T., & Teng, Y. (2024). Cyberbiosecurity: Advancements in DNA-based information security. Biosafety and Health, 6(4), 251–256. https://doi.org/10.1016/j.bsheal.2024.06.002
Pallardy, R. (2024, May 7). DNA is an Ancient Form of Data Storage. Is it Also a Radical New Alternative? https://www.informationweek.com/data-management/dna-is-an-ancient-form-of-data-storage-is-it-also-a-radical-new-alternative-
Center for Bioinformatics and Computational Biology | Houston Methodist. (n.d.). https://www.houstonmethodist.org/476_forhealthprofessionals/departments-programs-and-centers/499_forhealthcareprofessionals_departmentofcardiovascularsciences/centerbioinformaticscompbio/
Cao, B., Zheng, Y., Shao, Q., Liu, Z., Xie, L., Zhao, Y., Wang, B., Zhang, Q., & Wei, X. (2024). Efficient data reconstruction: The bottleneck of large-scale application of DNA storage. Cell Reports, 43(4), 113699. https://doi.org/10.1016/j.celrep.2024.113699




Comments